LI-FI Drained of More Than $10 Million By plan of Wallets With Limitless Approval Settings

On Tuesday, an attacker drained better than $10 million from a natty contract belonging to LI.FI, a DeFi protocol identified for its companies and products as a bridge and decentralized trade aggregator. The pockets address that exploited the natty contract has since transferred out nearly all the drained funds.
“A natty contract exploit earlier recently has been contained and the affected natty contract facet disabled,” LI.FI wrote on X at 11:44 a.m ET. “There’s currently no further probability to customers. The top most likely wallets affected were situation to limitless approvals, and represented most productive a genuinely little selection of customers.”
A natty contract exploit earlier recently has been contained and the affected natty contract facet disabled.
There’s currently no further probability to customers.
The top most likely wallets affected were situation to limitless approvals, and represented most productive a genuinely little selection of customers.
We’re fascinating…
— LI.FI (@lifiprotocol) July 16, 2024
According to blockchain analytics company Nansen, the pockets address that exploited LI.FI was in the starting build funded by Twister Money. Two of Twister Money’s main developers – Roman Storm and Roman Semenov – are going thru federal prosecution by the US Division of Justice for cash laundering. Meanwhile, a Dutch court docket rejected bail this week for Twister Money’s other developer, Alexey Pertsev, as reported by DLNews.
After the pockets address (0xd82) exploited a natty contract and acquired the funds drained from LI.FI, the exploiter proceeded to, among other actions, work along with decentralized trade Symbiosis, transact on Uniswap, and transfer thousands and thousands of dollars worth of ETH out to assorted addresses, onchain files reveals.
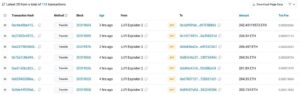
These seven transfers picture most definitely the most significant cash that was drained from LI-FI. (Etherscan)
How It Came about
According to Ido Ben-Natan, the CEO of crypto safety tools provider Blockaid, the attackers deceived LI.FI’s proxy contract – a router that mediates between customers and the protocol – into initiating unauthorized transfer commands to the protocol.
“The attackers have managed to milk a vulnerability in the proxy implementation. An attacker is ready to inject goal calls to the contract, which they’ve then aged to inject transfers from calls on approved customers,” Ben-Natan told Unchained over electronic mail. “What came about was that a proxy contract, which was aged as a relied on approval spender for swapping applications, got exploited into transferring approved resources to a malicious commute predicament.”
On X, the LI.FI team added that they’re additionally working with law enforcement and third parties to examine the crawl of funds that left the protocol.
Not LI.FI’s First Exploit
LI.FI has been the sufferer of unauthorized transfers sooner than.
According to safety company Peck Protect, the Tuesday’s exploit impacting LI.FI arose from in most cases the identical computer virus that had affected the identical protocol two years previously,
“While examining recently’s @lifiprotocol hack, we take into memoir[ed] an earlier hack on the identical protocol on March 20, 2022, wrote Peck Protect on X. “The computer virus is genuinely the identical.”
@Zord4n, who handles advertising for LI.FI based on their X profile, wrote on the day of the March 2022 hack about how a vulnerability prompted 29 wallets to lose a mixed complete of roughly $600,000.
“As a outcomes of the exploit, anybody who gave limitless approval to our contract was susceptible,” @Zord4n wrote in 2022.
On Tuesday, LI.FI team aged identical language in their post on X about how most productive wallets with limitless approval settings were impacted.
“We’re engaged on a post mortem that’ll catch you your complete files,” LI.FI founder and CEO Philipp Zentner told Unchained.
Source credit : unchainedcrypto.com
